Abstract
This document provides a thorough examination of an end-to-end cryptographic middleware designed for ASP.NET Core applications. The middleware facilitates secure message exchange between a client and a server by enforcing transport-layer security (HTTPS), verifying digital signatures, encrypting and decrypting request/response payloads at the application level, and preventing replay attacks via a nonce system stored in Redis. The primary cryptographic mechanisms include RSA for asymmetrical operations (key exchange, signing, and verifying signatures) and AES for symmetrical encryption of data. This text explains the theoretical underpinnings, architectural choices, detailed flow, and security implications of such a system, presenting it as a robust approach for organizations seeking to ensure data confidentiality, integrity, and authenticity in modern distributed environments.
Introduction
The proliferation of web-based services and microservice architectures necessitates advanced security measures that go beyond standard transport-layer protection. Although HTTPS (TLS) provides secure channel encryption, numerous scenarios demand additional layers of security at the application level. These scenarios include:
- End-to-End Data Encryption: Sensitive data must be inaccessible to intermediate proxies or load balancers, ensuring only the destination service can decrypt the payload.
- Replay Attack Prevention: Attackers might capture valid messages and reuse them, potentially causing unauthorized actions or duplicating requests.
- Selective Bypassing: Certain endpoints (e.g., health checks or public resources) might not require cryptographic overhead, making selective bypass desirable.
In response to these challenges, the described middleware embeds symmetric and asymmetric cryptography operations within the ASP.NET Core request pipeline. By maintaining a structured flow of certificate validation, key decryption, content decryption, signature checks, encryption of outbound content, and signature generation, the solution ensures robust and dynamic protection of in-flight data.
Architectural Overview
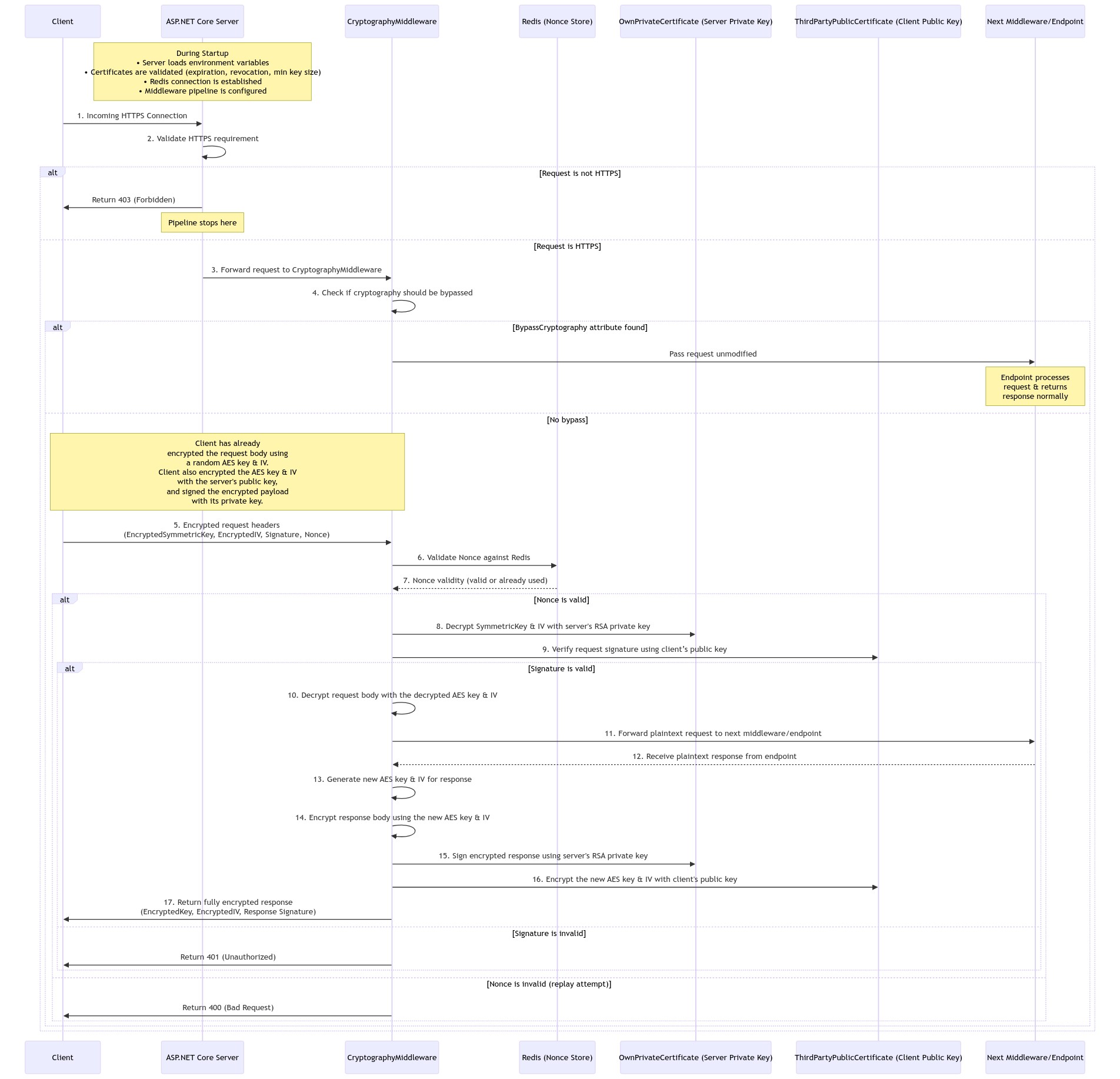
At a high level, the cryptographic middleware is inserted into the ASP.NET Core pipeline between the transport layer (HTTPS) and the eventual request-handling components (e.g., controllers, other middlewares). The architecture can be broken down into a series of steps whenever a request and response cycle occurs:
- Client-Side Preparation:
- The client encrypts its payload with a randomly generated AES key and initialization vector (IV).
- This AES key and IV are then encrypted with the server’s public RSA key (belonging to the middleware).
- The entire request payload is signed with the client’s private RSA key (or another private key from a third party the server trusts).
- A nonce is generated to prevent replay attacks, and both the payload and headers are sent over HTTPS.
- Server-Side Middleware:
- The middleware ensures the request is received over HTTPS (rejecting non-secure channels).
- It checks a nonce store (Redis in this implementation) to see if the nonce is new or has been used before, thus preventing replay attacks.
- The server decrypts the AES key and IV using its own private RSA key.
- The middleware verifies the client’s signature using the client’s public RSA certificate.
- The middleware decrypts the request payload using the newly decrypted AES key and IV.
- The request is forwarded to the next stage of the pipeline (a controller action or subsequent middleware) in plaintext format.
- After processing is complete and a response is generated, the middleware encrypts the response with a newly generated AES key and IV, signs the encrypted data, encrypts the new AES key and IV with the client’s public key, and returns the final encrypted response to the client.
- Nonce Storage (Redis):
- A short-lived key-value mapping ensures that any reused nonce is immediately recognized, which means subsequent requests containing the same nonce are rejected. This technique effectively blocks replayed payloads that might otherwise appear legitimate.
Key Components and Modules
Environment Variables and Configuration
To dynamically manage certificates and connection details, the middleware relies on environment variables:
- OWN_CERTIFICATE_PATH: The file path (or secret path) to the server’s private certificate (in PKCS#12/PFX format).
- OWN_CERTIFICATE_PASSWORD: The passphrase or password needed to load the private certificate.
- THIRD_PARTY_CERTIFICATE_PATH: The file path to the client’s (or other trusted party’s) public certificate, used for signature verification and key encryption.
- REDIS_CONNECTION_STRING: The network and authentication parameters for connecting to a Redis instance.
- NONCE_TTL_MINUTES: The time-to-live (TTL) for a given nonce in Redis. Once the TTL elapses, the nonce expires, preventing indefinite storage.
Retrieving these values at runtime permits secure storage of sensitive data (e.g., in environment variables, orchestrators, or secret management systems) and straightforward reconfiguration without redeploying the code.
Certificate Validation and Key Size Enforcement
Upon initialization, the middleware performs stringent checks on the loaded certificates:
- Expiry and Validity: Ensures that the certificate’s valid range covers the current system time. If the certificate is expired or not yet valid, the middleware rejects the configuration to avoid insecure operation.
- Revocation Checking: Establishes whether the certificate is still valid by building a certificate chain and checking revocation lists or online revocation servers. If the certificate is revoked or otherwise untrusted, the middleware halts execution to prevent compromised certificates from being used.
- Minimum RSA Key Size: Confirms that the private key has an RSA key size (e.g., 2048 bits or higher). Modern guidelines, including those from NIST, recommend 2048 bits as a practical minimum to thwart brute-force attacks.
If any of these validations fail, an exception is thrown, thereby preventing the middleware from starting in an insecure state.
Nonce Verification (Replay Attack Prevention)
A key security feature is the nonce system. When a client sends a request, it includes a fresh nonce in the headers:
- The middleware checks Redis to see if this nonce has been used before.
- If the nonce does not exist in Redis, it is stored with a short expiration time (e.g., 5 minutes).
- If the nonce is found in Redis, the middleware interprets it as a replay attempt and promptly rejects the request.
This mechanism is essential in distributed and load-balanced environments, where multiple servers share a single cache or session store. By centralizing nonce checks, the system can scale horizontally without losing replay protection.
Request Decryption and Signature Validation
When a request arrives with an encrypted AES key and IV:
- Decryption of AES Key and IV:
The server’s private RSA key is used to decrypt the symmetric key and IV. RSA encryption with OAEP (Optimal Asymmetric Encryption Padding) employing SHA-256 ensures robust security and resistance to padding oracle attacks. - Signature Verification:
The payload itself is hashed (commonly with SHA-256), and the resulting hash is checked against the signature using the client’s or third party’s public RSA certificate with PSS (Probabilistic Signature Scheme) padding. If the verification step fails, the middleware concludes that the message was either altered or not signed by the expected private key. - Symmetric Decryption:
With a valid AES key and IV, the middleware decrypts the actual request body. The data is encrypted in CBC (Cipher Block Chaining) mode, typically with PKCS#7 padding. CBC mode ensures that each block of plaintext is XORed with the previous ciphertext block, adding complexity for an attacker attempting to decrypt or manipulate the data.
At this stage, the middleware can either pass the decrypted data to subsequent components or, if any step fails (e.g., if decryption or signature checks do not pass), it immediately terminates the request with an appropriate error status (e.g., HTTP 401 for signature issues).
Response Encryption and Signing
After the downstream application processes the plaintext request and produces a result (often JSON or other structured data), the middleware secures the response:
- Generation of a New AES Key:
A fresh, random AES key is created for each response, ensuring forward secrecy. If a key is compromised at any point, previous or subsequent communications remain protected. - Symmetric Encryption:
The response payload is encrypted in CBC mode with PKCS#7 padding using the newly generated key and a new IV. This ensures that each unique response has a unique initialization vector, preventing pattern analysis. - Signing the Encrypted Payload:
The server signs the encrypted response data with its private RSA key, again typically using SHA-256 for hashing and RSA-PSS for the signature. Clients can subsequently confirm the authenticity of the server’s response by verifying this signature with the server’s public certificate. - Encryption of the AES Key and IV:
To share the newly generated AES key with the client securely, the key is encrypted using the client’s public RSA certificate. This step ensures that only the client, possessing the corresponding private key, can decrypt and access the symmetric key needed to decode the response payload.
Finally, the middleware sets custom HTTP headers that contain:
- The signature of the encrypted payload (server-generated).
- The newly encrypted symmetric key.
- The newly encrypted initialization vector.
The client processes these values on receipt to decrypt and verify the server’s response.
Security Analysis
Confidentiality and Integrity
By employing a hybrid cryptographic system, the middleware ensures both confidentiality (through AES encryption) and integrity (through RSA signature validation). A sophisticated attacker capable of intercepting the encrypted traffic cannot decrypt or modify it without access to the necessary private keys and ephemeral AES keys.
Replay Attacks
Replay attacks are neutralized through the nonce mechanism. Each request includes a unique identifier that the server stores in Redis with an expiration time. If the attacker attempts to resend the same request, the reused nonce will be detected and rejected. This ensures that even if someone records valid encrypted messages, they cannot reapply them for malicious gain.
Certificate Management
Potential issues involving compromised keys, misconfigured certificate paths, or expired certificates are preemptively mitigated by validating each certificate’s chain of trust and revocation status. By setting a minimum RSA key length (2048 bits or above), the system aligns with contemporary cryptographic standards that protect against increasingly powerful computational attacks.
Potential Vulnerabilities and Mitigations
- Elliptic Curve Cryptography Misalignment: Although the current design uses RSA, it could be adapted to Elliptic Curve Cryptography (ECC) for smaller key sizes and comparable security. If an organization transitions to ECC, similar checks on key size and certificate validity remain crucial.
- Side-Channel Attacks: The software depends on the security of hardware and the .NET runtime to protect cryptographic operations from side-channel leaks (e.g., timing attacks). Production deployments in sensitive environments often rely on hardware security modules (HSMs) or secure enclaves to mitigate such risks.
- Redis Availability: The nonce strategy hinges on Redis uptime. If Redis becomes unavailable, the system can reject all cryptographically protected requests until the nonce-check mechanism is restored. While this design choice upholds security, it also introduces a single point of potential failure.
Performance Considerations
Implementing cryptographic operations at the application layer introduces additional overhead compared to plaintext processing. Key factors include:
- RSA Encryption/Decryption: Relatively expensive, particularly for large key sizes, but typically limited to small pieces of data (the AES key and IV). Bulk data encryption uses AES, which is significantly faster.
- AES Encryption/Decryption: Highly efficient on modern processors (often with AES-NI hardware acceleration). Even large payloads can be encrypted or decrypted with minimal performance impact relative to other potential overheads (e.g., network I/O).
- Signature Generation and Verification: RSA-PSS with SHA-256 consumes CPU resources in proportion to key size. The middleware performs signing and verification only once per request/response cycle, which is usually acceptable for typical enterprise traffic levels.
- Redis Interaction: The nonce check requires a network round-trip to Redis. While Redis is designed for low-latency operations, organizations with extreme throughput requirements should ensure optimized caching or cluster strategies.
Conclusion
Summary of Benefits
By integrating an application-layer cryptographic process into the ASP.NET Core pipeline, the system benefits from:
- End-to-End Data Protection: Attackers intercepting traffic in intermediate hops cannot decrypt or tamper with the payload if they lack the necessary keys.
- Robust Integrity Checks: Signatures prevent unauthorized modifications, reinforcing trust in data authenticity.
- Replay Attack Defense: Nonce usage disallows repeated consumption of the same encrypted payload.
- Flexible and Configurable: Environment variables let operators adjust parameters (certificate paths, Redis endpoints, TTL values) without rebuilding the code.
Future Enhancements
- Galois/Counter Mode (GCM): Integrating AES-GCM can provide built-in authenticated encryption without needing separate signature steps, potentially reducing complexity.
- Hardware Security Modules (HSMs): Offloading private key operations to a secure hardware module enhances protection against private key compromise.
- Scalable Key Management: Using a managed key vault (e.g., Azure Key Vault, AWS KMS) can centralize and automate certificate rotation, further increasing security posture.
- Distributed Nonce Validation: In massive, globally distributed systems, a multi-region or cluster-based Redis setup can enhance both availability and performance.
Final Thoughts
The described middleware demonstrates a thorough approach to securing client-server communication beyond standard transport encryption. Through a combination of RSA-based key exchange, AES-based bulk encryption, digital signatures, HTTPS enforcement, and nonce-driven replay protection, it addresses significant threats faced by modern microservices and API-driven architectures. While these strategies alone do not guarantee holistic security—administrative, operational, and network-layer controls are also vital—they represent an essential cornerstone in building a resilient, confidential, and trustworthy communication pipeline.
References
- NIST Special Publication 800-57: Official guidelines on key management and cryptographic best practices.
- OWASP Cheat sheets: Best practices for secure cryptographic storage, transport, and application-layer encryption.
- RFC 8017: The standard detailing RSA cryptography, including OAEP and PSS padding for encryption and signatures, respectively.
- Merlin, P. and Smith, J. (Year). Advanced Cryptography for Web Services. Journal of Secure Computing, 15(3), pp. 210–228.